Chinese malware 'Tough Progress' discovered that exploits Google Calendar to perform stealth C2 communication

Google's Threat Intelligence Group (GTIG) has announced that it has discovered that the Chinese government-backed hacker group 'APT41' has used malware to write encrypted commands to Google Calendar and use it for
Mark Your Calendar: APT41 Innovative Tactics | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/apt41-innovative-tactics?hl=en
APT41 malware abuses Google Calendar for stealthy C2 communication
https://www.bleepingcomputer.com/news/security/apt41-malware-abuses-google-calendar-for-stealthy-c2-communication/
The malware attacks begin witha spear-phishing email sent to the target, which links to an archive hosted on a compromised government website. When unzipped, the archive extracts malware disguised as an export application document and an image attachment.
Below is the content of the malware compressed file released by Google. The ZIP file contains a shortcut file (.lnk) disguised as a PDF file, which when opened by a target opens an encrypted malware payload disguised as an image file, as well as a DLL file used to decrypt and launch the payload.
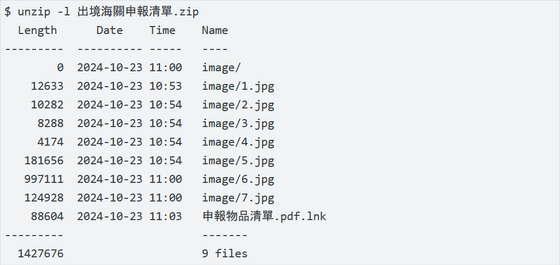
Google explains, ''6.jpg' and '7.jpg' are fake images. The first file is actually the encrypted payload that is decrypted by the second file, which is a DLL file that is launched when the target clicks on the shortcut file.'
The malware that has infiltrated the target device creates an event on a specific date (May 30, 2023) in the Google Calendar managed by the attacker, and writes data collected from the victim's device in the description. The malware then polls the calendar (checks it periodically), retrieves and executes encrypted commands from events on dates (July 30 and 31, 2023) that the attacker has created in advance, and creates a new calendar event while sending the victim's data to the attacker.
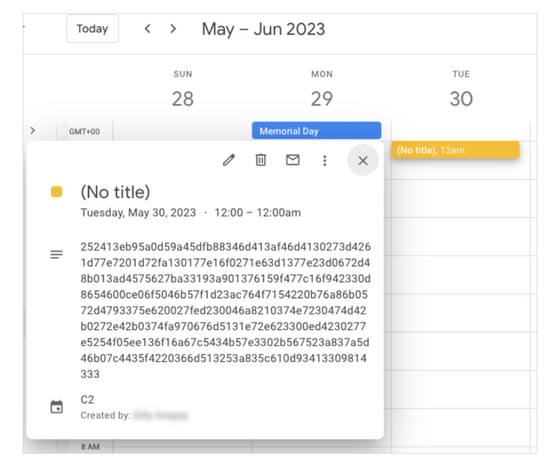
Using Google Calendar in the attack and performing the C2 attack via a legitimate cloud service allows the malware to carry out the attack without touching any of the target device's storage, minimizing the risk of being detected by the victim's device's security system. This is the basic mechanism of the stealth C2 attack observed this time.
While the names of the government organizations and victims involved have not been disclosed, Google has contacted them and provided them with information about the malware so that they can pinpoint the exact source of the infection. To prevent future use in similar attacks, Google has also taken down the attacker-controlled Workspace project, effectively dismantling the infrastructure APT41 used in this attack. The domains used in the attack have also been added to the Google Safe Browsing blocklist.
This is not the first time Google Calendar has been exploited in a C2 attack; on May 15, 2025, security firm Veracode reported on an npm attack employing similar tactics.
APT41 has also previously used Google services in attacks, and the malware ' Voldemort ' discovered in April 2023 and attacks using it exploited Google Sheets and Google Drive.
in Security, , Posted by log1l_ks