LockBit, known for the ransomware attack on Nagoya Port, was hacked and 59,975 BTC addresses and 4,442 victim negotiations were leaked onto the dark web

The infamous ransomware group LockBit, known for
LockBit ransomware gang hacked, victim negotiations exposed
https://www.bleepingcomputer.com/news/security/lockbit-ransomware-gang-hacked-victim-negotiations-exposed/
When Hackers Get Hacked: Analyzing the Breach of LockBit | by SlowMist | May, 2025 | Medium
https://slowmist.medium.com/when-hackers-get-hacked-analyzing-the-breach-of-lockbit-23b8f553747d
The LockBit ransomware site was breached, database dump was leaked online
https://securityaffairs.com/177619/cyber-crime/the-lockbit-ransomware-site-was-breached-database-dump-was-leaked-online.html
LockBit Ransomware Hacked, Insider Secrets Exposed - Infosecurity Magazine
https://www.infosecurity-magazine.com/news/lockbit-ransomware-hacked-insider/
LockBit Ransomware Hacked: Database and Victim Chats Leaked - Security Boulevard
https://securityboulevard.com/2025/05/lockbit-ransomware-hacked-database-and-victim-chats-leaked/
LockBit's Dark Web Domains Hacked, Internal Data and Wallets Leaked
https://hackread.com/lockbits-dark-web-domains-hacked/
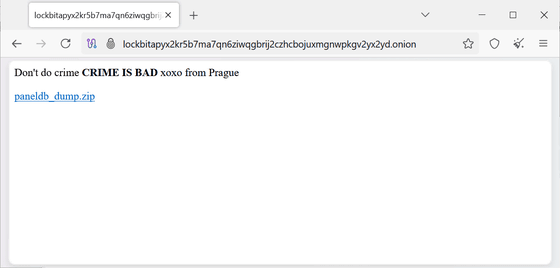
LockBit was hacked, the administration panel of the website it operates on the dark web was tampered with, and dump data of the MySQL database operated by the group was leaked.
The LockBit admin panel displayed the message 'Stop crime! Crime is bad! XOXO Prague' and included a link to download a dump of the MySQL database.
The first report that LockBit had been hacked was made by another threat actor, Rey.
So LockBit just got pwned... xD
pic.twitter.com/Jr94BVJ2DM — Rey (@ReyXBF) May 7, 2025
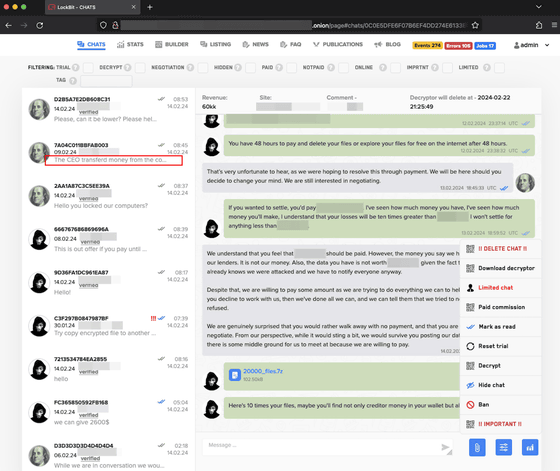
According to an analysis by security media BleepingComputer, the leaked dump data contained some interesting data, such as:
59,975 unique Bitcoin addresses.
Individual builds and public keys of ransomware created by affiliates for ransomware attacks. Although private keys were not included, some builds also included the names of targeted companies.
- Various configuration information used for each build, such as which ESXi servers LockBit should skip and which files it should encrypt.
75 administrators with access to the affiliate panel and information about affiliates. According to software developer Michael Gillespie , affiliate-related passwords were stored in plain text, and passwords such as 'Weekendlover69,' 'MovingBricks69420,' and 'Lockbitproud231' were used.
- 4,442 messages exchanged between LockBit and victims between December 19, 2024 and April 29, 2025.
LockBitSupp, the operator of LockBit, reported to Rey that they had investigated the damage immediately after the hack and found that no private keys had been leaked or data had been lost.
Response From LockBitSupp (This is a translated image):
pic.twitter.com/l54g1A5hXz — Rey (@ReyXBF) May 7, 2025
The leaked MySQL database dump data was created on April 29, 2025, and the security research group vx-underground has confirmed that the dump data is legitimate.
Lockbit ransomware group has been compromised. Their backend panel was dumped.
— vx-underground (@vxunderground) May 8, 2025
You can see my build logs in the data dump.
Lockbit gave me access after I sent him a bunch of cat pictures. pic.twitter.com/G1F3mhs6u7
It is unclear who hacked LockBit, but BleepingComputer points out that it is likely the same people who hacked the ransomware group 'Everest,' because the message displayed on the administration panel was exactly the same as the message displayed on the Everest website.
A security analyst who spoke to security media Hackread speculated that the LockBit hack was either a 'rival cybercrime group' or a ' hacktivist with insider knowledge,' because the level of skill required to tamper with the administration panels of multiple websites on the dark web and extract sensitive data goes beyond mere honor hacking, he explained.
LockBit has launched ransomware attacks against targets such as the Port of Nagoya, aerospace manufacturerBoeing , and the Italian Internal Revenue Service , but in 2024, an international investigation was carried out by the law enforcement unit 'Operation Kronos,' which includes law enforcement agencies from 10 countries, including Japan. As a result, LockBit's website was seized , its operator was arrested, and many decryption keys to decrypt the ransomware were successfully obtained.
FBI obtains over 7,000 decryption keys in crackdown on cybercrime group 'LockBit' - GIGAZINE

Meanwhile, LockBit has rebuilt its organization, restarted its RaaS offering, and even advertised updates to its ransomware, making it appear as though it's back.
However, this incident has 'further damaged LockBit's tarnished reputation. It is unclear whether this hack will be the final blow to bring LockBit's reputation to the ground,' BleepingComputer pointed out. Hackread reported, 'This incident not only sets back LockBit's efforts so far, but also reveals vulnerabilities that could be exploited again in attacks.'
Related Posts:
in Security, Posted by logu_ii






